
Top benefits of SOAR tools, plus potential pitfalls to consider
As organizations around the world face a constant and dynamic barrage of cybersecurity threats, the development of tools to accelerate security operations, automation and response, or SOAR, has rapidly increased.
According to the FBI’s Internet Crime Complaint Center 2020 Internet Crime Report, cybercrime resulted in more than $4.2 billion in annual losses, and most infosec teams are struggling to keep up due to limited resources and head count. Overextended teams may also have accumulated numerous, often disparate, security tools to contain the firehose of threats — each of which must be monitored, analyzed and triaged.
SOAR tools are designed for the following functions:
- Security orchestration connects and coordinates heterogeneous tool sets and defines incident analysis parameters and processes.
- Automation automatically triggers specific workflows, tasks and triages based on those parameters, including automated steps for lower-risk incidents.
- Response accelerates general and targeted responses by enabling a single view for analysts to access, query and share threat intelligence.
There are two main business incentives for adopting SOAR tools in security programs. First, SOAR centralizes visibility and insights into threats. Second, it simultaneously manages the more low-level incidents to support and scale human analysts. From these upstream motivations flow several downstream affects security leaders must consider.
Compare SOAR benefits vs. drawbacks
To achieve the benefits of SOAR and avoid potential pitfalls, it behooves organizations to first look beyond the tools and technology. No technology is a silver bullet for fixing broken security culture or alleviating antagonized and depleted infosec teams. Additionally, a Band-Aid deployment will not mitigate a lack of security strategy, nor outdated or patchwork tools and information.
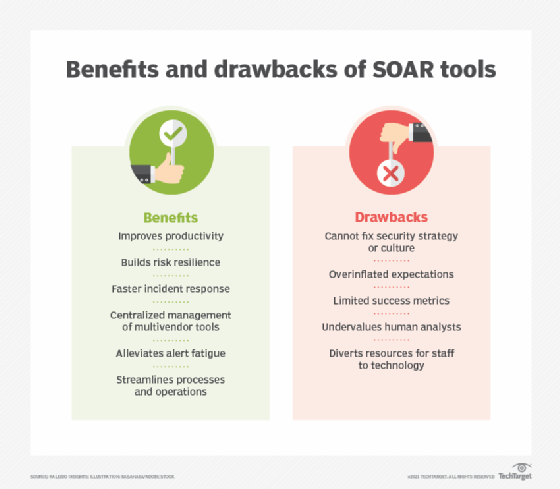
SOAR benefits
Though adoption success may vary depending on the organization, security leaders can anticipate the following benefits of SOAR implementation:
- improved productivity;
- less tedious and repetitive work for humans;
- more strategic allocation for human analysts;
- process and operational efficiencies in alerts and triage;
- faster incident response and remediation;
- centralized and coordinated multivendor security tools and analytics; and
- increased resilience against growing threat landscape.
SOAR drawbacks
To help set expectations regarding SOAR adoption and capabilities, bear in mind the following potential pitfalls:
- inability to assess broader security maturity or integrate into strategy;
- failure to address the security culture;
- undervaluing of human analysts in favor of software;
- redirection of staff resources to technology resources;
- overinflation of expectations for SOAR capabilities and intelligence;
- potential mistaken conflation with AI; and
- limited or unclear success metrics.
SOAR adoption considerations
To ensure successful SOAR adoption, security leaders need to identify objectives the tools will advance, how those objectives align to broader strategy and how success will be measured. For example, orchestration, a core capability of SOAR, helps coordinate multivendor security infrastructure. This objective often aligns with the strategic need for visibility and management across large-scale enterprise security topologies. Potential metrics are not limited to time-centric measurements, but can also support vendor management, identifying redundancies, analyst workflows, compliance and unidentified permissions or devices, among other KPIs. Connecting these dots is as important for success as the technical integration.
It is also essential to understand SOAR not only as an enterprise tool for sheer efficiency gains, but foremost as a tool to empower human analysts. SOAR tools typically focus on common security scenarios and highly repetitive front-end steps, such as basic alert enrichment or triggering an alert on Slack. Because they do not defend against anomalous scenarios and are not tools for highly nuanced investigations, SOAR tools cannot replace security pros or compensate for talent shortfalls. The utility of SOAR is to lighten the load by reducing the manual effort associated with alert overload and automating the tedium of proactive risk mitigation. Successful adoption frees up highly skilled analysts to focus on more challenging assignments, emergent threats and higher-risk incidents.
Security organizations must meet ever-increasing cyber threats with agile and adaptive security postures and infrastructure. While any form of security automation offers inherent efficiencies, SOAR technologies can compound that value by elevating the combination of human and machine strengths.