
U.S. agencies continue to observe Volt Typhoon intrusions
SAN FRANCISCO — Experts warned that Volt Typhoon will pose a persistent threat to critical infrastructure organizations as well as small to medium-sized enterprises for years to come.
During an RSA Conference 2024 session on Monday, panelists discussed the threat posed by the Chinese nation-state threat group tracked as Volt Typhoon by Microsoft. Cynthia Kaiser, deputy assistant director for the FBI, moderated the session, which featured panelists Morgan Adamski, director of the National Security Agency (NSA) Cybersecurity Collaboration Center; Sherrod DeGrippo, director of threat intelligence strategy for Microsoft; and Andrew Scott, associate director for China operations at CISA.
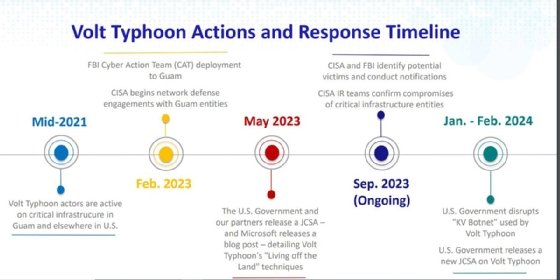
Volt Typhoon has emerged as a dangerous threat over the last year. In February CISA warned the group had compromised critical infrastructure organizations and maintained access to some victim’s IT environments for at least five years.
With no evidence of cyberespionage motives, U.S. agencies warned that Volt Typhoon was maintaining the access to critical infrastructure networks in case of a major conflict with the U.S. In a March advisory, CISA issued mitigation recommendations for critical infrastructure organizations as the threat continues.
“Volt Typhoon is not a ‘this month’ problem. It is going to be a problem for multiple years, and we are seeing Volt Typhoon activity every single day. We are learning about new intrusions,” Adamski said during the session.
She credited an operational collaboration between the public and private sectors for the discovery of Volt Typhoon. The sharing of information was crucial because of Volt Typhoon’s evasion techniques, such as not using malware during attacks. Adamski said at least 11 industry partners contributed to the February alert.
However, she also stressed that many enterprises had trouble dissecting the technical advisory that outlined Volt Typhoon’s tactics, techniques, and procedures. The advanced persistent threat (APT) group maintains persistent access to victims’ environments by using uses living off the land (LOTL) tactics, where attackers abuse legitimate software and command line tools to bypass security protections and move laterally inside networks. Enterprises can’t rely on endpoint detection and response products to flag LOTL activity, and Volt Typhoon is adept at obfuscating logging activity.
Adamski said a big problem that hinders protections against the nation-state threat group is that network owners can’t use or understand the technical advisories.
“I can’t tell you the amount of times we’d go talk about Volt Typhoon and we’d talk about the security advisory and people would raise their hands and say, ‘Can you just send me the indicators list, and I’ll look at my logs?’
“We said, ‘No, that’s not what we’re talking here.’ It’s living off the land. We’re talking about identity and access management. This is about understanding when your system admins are on the network and when they’re not,” she said.
‘Significant edge device problem’
Scott warned that Volt Typhoon commonly targets email gateways and routers, which are edge devices that reside on the external part of a network. Once they have access to such devices, they have access to the victim’s network, he said. Another way Volt Typhoon gained access to victims’ networks was by compromising Microsoft’s Active Directory (AD).
CISA observed the threat actor exfiltrated files from the AD where credentials were stored. However, they did it periodically to avoid detection. Once they gained an authenticated users’ credentials, they’d return a month later and leverage whatever that user’s access granted.
“What we saw in the pattern of targeting and incident response was smaller to medium-sized businesses who were critical enablers of other critical infrastructure,” Scott said.
DeGrippo said that the use of LOTL techniques is a growing trend across the threat landscape. She stressed that “this is a new world now” where threat actors from every nation are combining LOTL tactics with residential proxies to conduct attacks. The Justice Department announced in December that it had disrupted Volt Typhoon’s botnet of hundreds of U.S.-based SOHO routers, which the group used to attack critical infrastructure targets. Additionally, other nation-state groups, such as Russia’s APT29, also known as Cozy Bear and Midnight Blizzard, have also used residential proxies to conceal their activity.
When Kaiser asked DeGrippo what she’s currently telling her Microsoft customers, DeGrippo said it’s urgent to patch edge devices. “We have an edge device problem on the threat landscape. It is significant,” DeGrippo said.
She said that enterprises continue to use end of life and legacy devices that Volt Typhoon targets as well. To combat Volt Typhoon threat activity, the panelists stressed the importance of responding to alerts and having leadership plans in place before an attack occurs. DeGrippo said if CISA, the NSA or the FBI is calling, enterprises better answer the phone because “it’s a different level of urgency.”
The panelists also urged enterprises to implement detailed logging as well as enhance IT and operational technology segmentation.
The edge device problem was highlighted in a report by cyber insurer Coalition last month. The company warned that enterprises using Cisco and Fortinet devices faced a greater risk of attacks because the devices contained more vulnerabilities and enterprises struggle with timely patch management.
Tim Mackey, head of software supply chain risk strategy at Synopsys, said to TechTarget Editorial he advises his team to test edge devices on the inside to see what gets through and compare notes. “What did it filter out, what didn’t it filter out? Is there a way to exploit something that got filtered out from the inside? We need to start having those kinds of conversations,” Mackey said.
The panelists said that Volt Typhoon will be a long-term threat that could become increasingly dangerous as time goes on. DeGrippo expressed concern about how Volt Typhoon and other nation-state groups could abuse AI tools like large language models (LLM) to enhance their operations.
“I really think this is all going to accelerate, and I think this is going to accelerate because of AI,” she said. “Take that exfiltrated data and train an LLM on it and you can search it faster than you can blink your eyes. That’s something that I think a lot of people need to think about.”
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.