
What is transport layer? – Definition from WhatIs.com
Positioned at Layer 4 of the Open Systems Interconnection (OSI) communications model, the transport layer ensures the reliable arrival of messages across a network and provides error-checking mechanisms and data flow controls.
The transport layer takes application messages and transmits those message segments into Layer 3, the networking layer. Once the receiving side has the segments, they are reassembled into messages and passed on to Layer 7, the application layer.
The functions of the transport layer
Connection mode and connectionless mode transmissions. For connection mode transmissions, a transmission may be sent or arrive in the form of packets that need to be reconstructed into a complete message at the other end. Connection mode transmissions also require acknowledgement from the receiving device as an assurance.
The Transmission Control Protocol (TCP) is the most common form of connection-oriented transmission today. The connections are identified and tracked using port numbers that range between 0 and 65,535. One useful benefit of TCP is that it uses a positive acknowledgement with retransmission technique where the receiving device must respond back to the sender that it indeed received the data it was sent.
If the sender does not receive this acknowledgement message, it assumes the receiving device did not receive all or part of the transmission — and thus attempts to resend the data. FTP is a great example of a connection-mode application that can take advantage of positive acknowledgement, as you want to be completely sure the receiving device receives every packet when transmitting files.
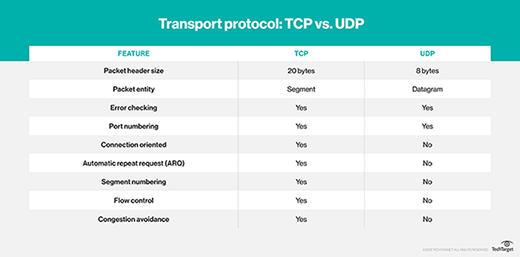
The User Data Protocol (UDP) is an example of a connectionless-oriented protocol. Similar to TCP, UDP uses port numbers between 0 and 65,535 for identification and tracking of data transmission streams. But unlike TCP, which requires acknowledgement from the receiving device, UDP provides no guarantee mechanism. Because of this, UDP is ideal for real-time, streaming data transmissions, like voice and video conferencing.
Same order delivery. This makes sure packets are delivered in a specific sequence. Each packet is given a number and the receiver reorders the packets.
Data integrity. There are various ways packets might be lost or corrupted. Packets may also be delivered in the wrong order. Through the use of error detection codes, such as a checksum, the transport layer ensures the data is not corrupted by sending an acknowledgement message to the sender.
Flow control. The sending device may transmit data at a faster rate than the memory capacity on the receiving device is able to process. In order to avoid having the receiving device overwhelmed with data, flow control manages the traffic so that it’s at an acceptable rate. It also addresses data flow when the receiver isn’t getting data fast enough.
Congestion avoidance. The transport layer manages traffic and circumvents congestion by understanding where nodes or links are oversubscribed and then taking the proper steps to reduce the rate at which packets are sent, among other remedies.
Multiplexing. Packet streams can come from unrelated applications and a variety of sources. This permits the use of different applications or services across a network, such as when a user opens different browsers on the same computer.